VLANs key notes
The following list summarizes the most common reasons for choosing to create smaller broadcast domains (VLANs):
- To reduce CPU overhead on each device, improving host performance, by reducing the number of devices that receive each broadcast frame.
- To reduce security risks by reducing the number of hosts that receive copies of frames that the switches flood (broadcast, multicast, and unknown unicasts).
- To improve security for host through the application of different security policies per VLAN.
- To create more flexible designs that group users by department, or by groups that work together, instead of by physical location.
- To solve problems more quickly, because the failure domain is reduced (many problems are in the same set of devices in the same broadcast domain).
- To reduce the workload for STP by limiting a VLAN to a single access switch.
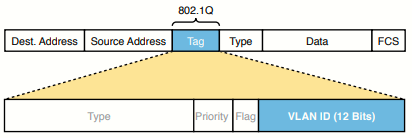
802.1Q inserts an extra 4-byte 802.1Q VLAN header into the original frame’s Ethernet header.
All switches can use normal-range VLANs (1-1005). Only some switches can use extended-range VLANs (1006-4094), and it depends on VTP configuration.
The native VLAN has no trunking header. Meant for a device connected to a switch that does not understand 802.1Q trunking.
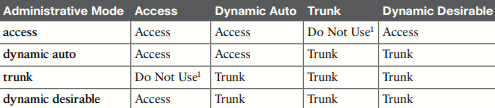
Regarding trunking, switch ports usually default to dynamic auto.
Phones:
- Voice VLAN: The VLAN defined on the link for forwarding the phone's traffic. Traffic in this VLAN is typically tagger with an 802.1Q header.
CDP must be enabled on an interface for a voice access port to work with Cisco IP phones. Cisco switches and routers enable CDP by default.