Network Virtualization
Cloud Computing versus Data Center
The terms data center and cloud computing are often used incorrectly. These are the correct definitions of data center and cloud computing:
- Data center: Typically, a data storage and processing facility run by an in-house IT department or leased offsite.
- Cloud computing: Typically, an off-premise service that offers on-demand access to a shared pool of configurable computing resources. These resources can be rapidly provisioned and released with minimal management effort.
Data centers are the physical facilities that provide the compute, network, and storage needs of cloud computing services. Cloud service providers use data centers to host their cloud services and cloud-based resources.
A data center can occupy one room of a building, one or more floors, or an entire building. Data centers are typically very expensive to build and maintain. For this reason, only large organizations use privately built data centers to house their data and provide services to users. Smaller organizations that cannot afford to maintain their own private data center can reduce the overall cost of ownership by leasing server and storage services from a larger data center organization in the cloud.
Virtualization
Virtualization is the foundation of cloud computing. Virtualization separates the operating system (OS) from the hardware.
Server sprawl: Servers sitting idle for long periods of time, wasting energy, taking space.
The hypervisor is a program, firmware, or hardware that adds an abstraction layer on top of the physical hardware. The abstraction layer is used to create virtual machines which have access to all the hardware of the physical machine.
Advantages of Virtualization
- Less equipment, energy and space used.
- Easier prototyping.
- Faster server provisioning
- Increased server uptime
- Improved disaster recovery
- Legacy support
Abstraction layers
A computer consists of the following abstraction layers:
- Services
- OS
- Firmware
- Hardware
At each of these layers of abstraction, some type of programming code is used as an interface between the layer below and the layer above. A hypervisor is installed between the firmware and the OS. The hypervisor can support multiple instances of OSs.
Some management consoles (used with Type 1 hypervisors) allow server over allocation. Over allocation is when multiple OS instances are installed, but their memory allocation exceeds the total amount of memory that a server has. For example, a server has 16 GB of RAM, but the administrator creates four OS instances with 10 GB of RAM allocated to each. This type of over allocation is a common practice because all four OS instances rarely require the full 10 GB of RAM at any one moment.
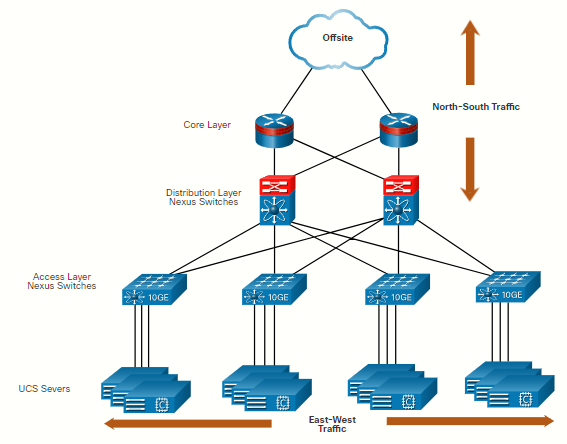
Data Center Traffic Flows
- East-West traffic: Typically, a DC has a considerable amount of traffic being exchanged between virtual servers. These flows can change in location and intensity over time.
- North-South traffic: Occurs between the distribution and core layers and is typically traffic destined for offsite locations such as another data center, other cloud providers, or the internet.
Network functions can be virtualized. Each network device can be segmented into multiple virtual devices that operate as independent devices. Examples include subinterfaces, virtual interfaces, VLANs, and routing tables. Virtualized routing is called virtual routing and forwarding (VRF).
Control Plane and Data Plane
A network device contains the following planes:
- Control plane: It is used to make forwarding decisions. Contains L2 and L3 route forwarding mechanisms, such as routing protocol neighbor tables and topology tables, IPv4 and IPv6 routing tables, STP, and the ARP table. Information sent to the control plane is processed by the CPU.
- Data plane: Also called the forwarding plane, this is typically the switch fabric connecting the various network ports on a device. The data plane of each device is used to forward traffic flows. Routers and switches use information from the control plane to forward incoming traffic out the appropriate egress interface. Information in the data plane is typically processed by a special data plane processor without the CPU getting involved.
CEF is an advanced, L3 IP switching technology that enables forwarding of packets to occur at the data plane without consulting the control plane. In CEF, the control plane’s routing table pre-populates the CEF Forwarding Information Base (FIB) table in the data plane. The control plane’s ARP table pre-populates the adjacency table. Packets are then forwarded directly by the data plane based on the information contained in the FIB and adjacency table, without needing to consult the information in the control plane.
SDN is basically the separation of the control plane and data plane. The control plane function is removed from each device and is performed by a centralized controller, as shown in the figure. The centralized controller communicates control plane functions to each device. Each device can now focus on forwarding data while the centralized controller manages data flow, increases security, and provides other services.
- Management plane: Responsible for managing a device through its connection to the network with SSH, TFTP, SFTP, HTTPS, SNMP... to access the management plane and configure the device.
Network Virtualization Technologies
Two major network architectures have been developed to support network virtualization:
- Software-Defined Networking (SDN): A network architecture that virtualizes the network, offering a new approach to network administration and management that seeks to simplify and streamline the administration process.
- Cisco Application Centric Infrastructure (ACI): A purpose-built hardware solution for integrating cloud computing and data center management.
Components of SDN may include the following:
- OpenFlow: [RELLENAR]
- OpenStack: A virtualization and orchestration platform designed to build scalable cloud environments and provide an IaaS solution. OpenStack if often used with Cisco ACI. Orchestration in networking is the process of automating the provisioning of network components such as servers, storage, switches, routers, and applications.
- Other components: Interface to the Routing System (I2RS), Transparent Interconnection of Lots of Links (TRILL), Cisco FabricPath (FP), and 802.1aq Shortest Path Bridging (SPB).
Traditional vs SDN Architectures
In a traditional router or switch architecture, the control plane and data plane functions occur in the same device. Routing decisions and packet forwarding are the responsibility of the device operating system. In SDN, management of the control plane is moved to a centralized SDN controller. The figure compares traditional and SDN architectures.
The SDN controller is a logical entity that enables network administrators to manage and dictate how the data plane of switches and routers should handle network traffic. It orchestrates, mediates, and facilitates communication between applications and network elements.
The complete SDN framework is shown in the figure. Note the use of Application Programming Interfaces (APIs) within the SDN framework. An API is a set of standardized requests that define the proper way for an application to request services from another application. The SDN controller uses northbound APIs to communicate with the upstream applications. These APIs help network administrators shape traffic and deploy services. The SDN controller also uses southbound APIs to define the behavior of the data planes on downstream switches and routers. OpenFlow is the original and widely implemented southbound API.

SDN Controller and Operations
The SDN controller defines the data flows between the centralized control plane and the data planes on individual routers and switches.
Each flow traveling through the network must first get permission from the SDN controller, which verifies that the communication is permissible according to the network policy. If the controller allows a flow, it computes a route for the flow to take and adds an entry for that flow in each of the switches along the path.
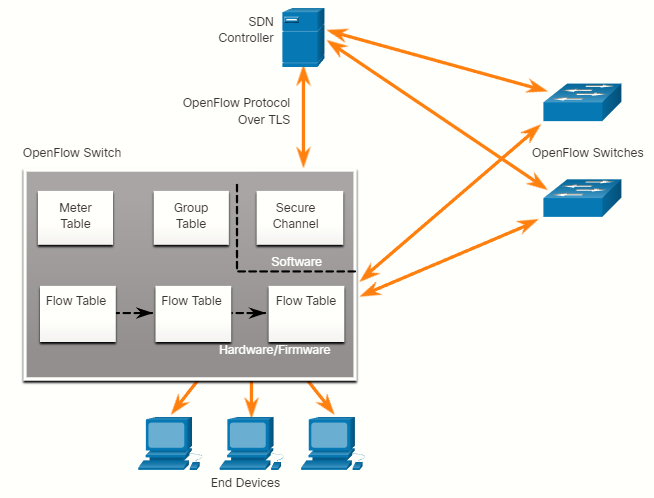
All complex functions are performed by the controller. The controller populates flow tables. Switches manage the flow tables. In the figure, an SDN controller communicates with OpenFlow-compatible switches using the OpenFlow protocol. This protocol uses TLS to securely send control plane communications over the network. Each OpenFlow switch connects to other OpenFlow switches. They can also connect to end-user devices that are part of a packet flow.
Within each switch, a series of tables implemented in hardware or firmware are used to manage the flows of packets through the switch. To the switch, a flow is a sequence of packets that matches a specific entry in a flow table.
The three tables types shown in the previous figure are as follows:
- Flow table: Matches incoming packets to a particular flow and specifies the functions that are to be performed on the packets. There may be multiple flow tables that operate in a pipeline fashion.
- Group table: A flow table may direct a flow to a group table, which may trigger a variety of actions that affect one or more flows.
- Meter table: This table triggers a variety of performance-related actions on a flow including the ability to rate-limit the traffic.
Cisco ACI
These are the three core components of the ACI architecture:
- Application Network Profile (ANP): An ANP is a collection of end-point groups (EPG), their connections, and the policies that define those connections. The EPGs shown in the figure below, such as VLANs, web services, and applications, are just examples. An ANP is often much more complex.
- Application Policy Infrastructure Controller (APIC): The APIC is considered to be the brains of the ACI architecture. APIC is a centralized software controller that manages and operated a scalable ACI clustered fabric. It is designed for programmability and centralized management. It translates application policies into network programming.
- Cisco Nexus 9000 Series Switches: These switches provide an application-aware switching fabric and work with an APIC to manage the virtual and physical network infrastructure.
The APIC is positioned between the APN and the ACI-enabled network infrastructure. The APIC translated the application requirements into a network configuration to meet those needs.
The Cisco ACI fabric is composed of the APIC and the Cisco Nexus 9000 series switches using two-tier spine-leaf topology. The leaf switches always attach to the spines, but they never attach to each other.
Similarly, the spine switches only attach to the leaf and core switches (not shown). In this two-tier topology, everything is one hop from everything else.
The Cisco APICs and all other devices in the network physically attach to leaf switches.
When compared to SDN, the APIC controller does not manipulate the data path directly. Instead, the APIC centralizes the policy definition and programs the leaf switches to forward traffic based on the defined policies.
SDN Types
The Cisco APIC-EM (Enterprise Module) extends ACI aimed at enterprise and campus deployment. To better understand APIC-EM, it is helpful to take a broader look at the three types of SDN:
Device-based SDN
In this type of SDN, the devices are programmable by applications running on the device itself or on a server in the network. Cisco OnePK is an example of a device-based SDN. It enables programmers to build applications using C, and Java with Python, to integrate and interact with Cisco devices.
Controller-based SDN
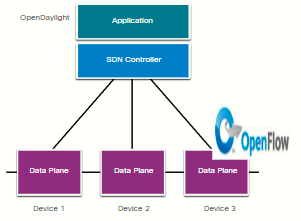
This type of SDN uses a centralized controller that has knowledge of all devices in the network. The applications can interface with the controller responsible for managing devices and manipulating traffic flows throughout the network. The Cisco Open SDN Controller is a commercial distribution of OpenDaylight.
Policy-based SDN
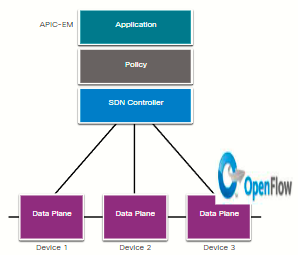
This type of SDN is similar to controller-based SDN where a centralized controller has a view of all devices in the network, as shown in the figure. Policy-based SDN includes an additional Policy layer that operates at a higher level of abstraction. It uses built-in applications that automate advanced configuration tasks via a guided workflow and user-friendly GUI. No programming skills are required. Cisco APIC-EM is an example of this type of SDN.
|
Device-based SDN |
Controller-based SDN |
Policy-based SDN |
APIC-EM
Each type of SDN has its own features and advantages. Policy-based SDN is the most robust, providing for a simple mechanism to control and manage policies across the entire network. Cisco APIC-EM is an example of policy-based SDN. Cisco APIC-EM provides a single interface for network management including:
- discovering and accessing device and host inventories
- viewing the topology
- tracing a path between end points
- setting policies
The APIC-EM Path Trace tool allows the administrator to easily visualize traffic flows and discover any conflicting, duplicate, or shadowed ACL entries. This tool examines specific ACLs on the path between two end nodes, displaying any potential issues. You can see where any ACLs along the path either permitted or denied your traffic.