Securing Wireless Networks
Authentication
To use a wireless network, clients must first discover a basic service set (BSS) and then request permission to associate with it. Clients should be authenticated by some means before they can become functioning members of the wireless LAN. Guest users, if they are permitted at all, should be allowed to join a different guest WLAN where they can access nonconfidential or public resources. Rogue clients, which are not expected or welcomed, should not be permitted to associate at all.
Potential clients must identify themselves by presenting some form of credentials to the APs. Also, after associated to the AP, to prevent fake AP attacks, the client should authenticate the AP before authenticating itself. Even further, any mgmt frames received by a client should be authenticated too, as proof that they were sent by a legitimate and expected AP.
Wireless Client Authentication Methods
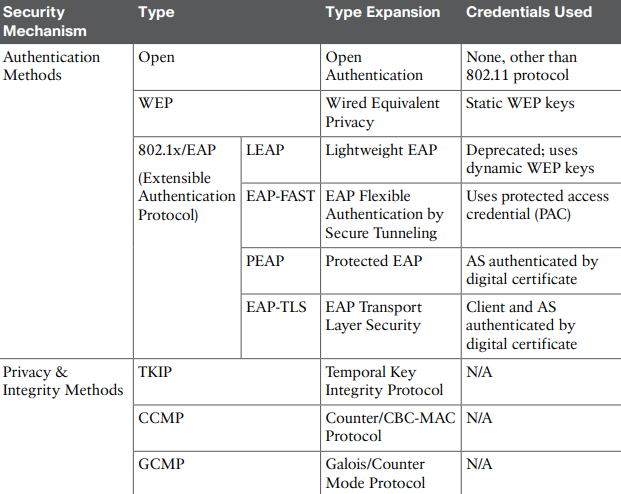
- Open authentication
- WEP
- 802.1x/EAP
Open authentication
The only requirement is that a client must use an 802.11 authentication request before it attempts to associate with an AP. No other credentials are needed. For use with captive portals nowadays.
WEP (Wired Equivalent Privacy)
Uses RC4 cipher algorithm to make every wireless data frame private and hidden from eavesdroppers. The same algorithm encrypts data at the sender and decrypts it at the receiver. The algorithm uses a string of bits as a key, WEP key, to derive other encryption keys (one per wireless frame). As long as the sender and receiver have an identical key, one can decrypt what the other encrypts.
WEP is known as a shared-key security method. The same key must be shared between the sender and receiver ahead of time, so that each can derive other mutually agreeable encryption keys. In fact, every potential client and AP must share the same key ahead of time so that any client can associate with the AP.
The WEP key can also be used as an optional authentication method as well as an encryption tool. Unless a client can use the correct WEP key, it cannot associate with an AP. The AP tests the client’s knowledge of the WEP key by sending it a random challenge phrase. The client encrypts the challenge phrase with WEP and returns the result to the AP. The AP can compare the client’s encryption with its own to see whether the two WEP keys yield identical results.
WEP keys can be either 40 or 104 bits long, represented by a string of 10 or 26 hex digits. As a rule of thumb, longer keys offer more unique bits for the algorithm, resulting in more robust encryption. Except in WEP's case. Both WEP encryption and WEP shared-key authentication are widely considered to be weak methods to secure a WLAN.
802.1x/EAP
Rather than build additional authentication methods into the 802.11 standard, a more flexible and scalable authentication framework, the Extensible Authentication Protocol (EAP) was chosen. As its name implies, EAP is extensible and does not consist of any one authentication method. Instead, EAP defines a set of common functions that actual authentication methods can use to authenticate users.
EAP has another interesting quality: it can integrate with the 802.1x port-based access control standard. When 802.1x is enabled, it limits access to a network media until a client authenticates. This means that a wireless client might be able to associate with an AP but will not be able to pass data to any other part of the network until it successfully authenticates. With open and WEP authentication, wireless clients are authenticated locally at the AP without further intervention. The scenario changes with 802.1x; the client uses open authentication to associate with the AP, and then the actual client authentication process occurs at a dedicated authentication server. 802.1x arrangement consists of the following entities:
- Supplicant: Client device requesting access
- Authenticator: Network device that provides access to the network (usually a WLC)
- Authentication server: Device that takes user/client credentials and permits or denies network access based on a user database and policies (usually a RADIUS server).
When you configure user authentication on a wireless LAN, you will not have to select a specific method between LEAP, EAP-FAST, PEAP or EAP-TLS. Instead, you select 802.1x on the WLC so that it is ready to handle a variety of EAP methods. It is then up to the client and the authentication server to use a compatible method.
Message privacy and integrity
After authentication, data passing to and from the client is still available to eavesdroppers on the same channel. Data should be encrypted. This is accomplished by encrypting the data payload in each wireless frame just prior to being transmitted, then decrypting it as it is received. The idea is to use an encryption method that the transmitter and receiver share, so the data can be encrypted and decrypted successfully.
In wireless networks, each WLAN may support only one authentication and encryption scheme, so all clients must use the same encryption method when they associate. You might think that having one encryption method in common would allow every client to eavesdrop on every other client. That is not necessarily the case because the AP should securely negotiate a unique encryption key to use for each associated client. Ideally, the AP and a client are the only two devices that have the encryption keys in common so that they can understand each other’s data. No other device should know about or be able to use the same keys to eavesdrop and decrypt the data.
The AP also maintains a "group key" that is uses when it needs to send encrypted data to all clients in its cell at one time. Each of the associated clients uses the same group key to decrypt the data.
A message integrity check (MIC) is a security tool that can protect against data tampering (manipulación).
Since WEP encryption has been deprecated, the following options are available to encrypt data and protect its integrity as it travels through free space:
TKIP (WPA)
When WEP was about to be discovered vulnerable, Temporal Key Integrity Protocol was developed. It adds the following security features using legacy hardware and the underlying WEP encryption:
- MIC: adds a hash value to each frame to prevent tampering.
- Time stamp: added into the MIC to prevent replay attacks.
- Sender's MAC address: the MIC also includes it as evidence of the frame source.
- TKIP sequence counter: provides a record of frames sent by a unique MAC address (prevents replay attacks).
- Key mixing algorithm: this algorithm computes a unique 128-bit WEP key for each frame.
- Longer initialization vector (IV): the IV size is double from 24 to 48 bits, making it virtually impossible to exhaust all WEP keys by brute-force calculation.
TKIP was a reasonably secure stopgap till WPA2 (802.11i) standard could be ratified. It was deprecated in 2012.
CCMP (WPA2)
Counter/CBC-MAC Protocol. Considered more secure than TKIP. Consists of two algorithms:
- AES counter mode encryption
- Cipher Block Chaining Message Authentication Code (CBC-MAC) used as a MIC
Before CCMP can be used to secure a wireless network, the client devices and APs must support the AES counter mode and CBC-MAC in hardware. CCMP cannot be used on legacy devices that support only WEP or TKIP.
GCMP (WPA3)
Galois/Counter Mode Protocol (GCMP) is a robust authenticated encryption suite that is more secure and more efficient than CCMP. GCMP consists of two algorithms:
- AES counter mode encryption
- Galois Message Authentication Code (GMAC) used as a MIC
WPA, WPA2, and WPA3
When it comes time to configure a WLAN with wireless security, should you try to select some combination of schemes based on which one is best or which is not deprecated? Which authentication methods are compatible with which encryption algorithms? The Wi-Fi Alliance worked out straightforward to do that through its Wi-Fi Protected Access (WPA) industry certifications.
The Wi-Fi Alliance introduced its first generation WPA certification while the 802.11i amendment was being developed. WPA was based on parts of 802.11i and included 802.1x authentication, TKIP, and a method for dynamic encryption key management.
Once 802.11i was ratified and published, the alliance included it in full in its WPA2 certification. WPA2 is based around the superior AES CCMP algorithms, rather than the deprecated TKIP from WPA.
WPA3 (2018) leverages stronger encryption by AES with GCMP. It also uses Protected Management Frames (PMF) to secure important 802.11 management frames between APs and clients, to prevent malicious activity that might spoof or tamper with a BSS's operation.
Notice all 3 WPA versions support two client authentication modes: a pre-shared key (PSK) or 802.1x, based on the scale of the deployment. These are also known as personal mode and enterprise mode, respectively. With personal mode, a key string must be shared or configured on every client and AP before the clients can connect to the wireless network. The pre-shared key is normally kept confidential so that unauthorized users have no knowledge of it. The key string is never sent over the air. Instead, clients and APs work through a four-way handshake procedure that uses the pre-shared key string to construct and exchange encryption key material that can be openly exchanged. Once that process is successful, the AP can authenticate the client and the two can secure data frames that are sent over the air.
With WPA and WPA2 personal modes, a malicious user can eavesdrop and capture the four-way handshake between a client and an AP. That user can then use a dictionary attack to automate guessing the PSK. If he is successful, he can then decrypt the wireless data or even join the network posing as a legitimate user. WPA3 personal avoids such an attack by strengthening the key exchange between clients and APs through a method known as Simultaneous Authentication of Equals (SAE). Rather than a client authenticating against a server or AP, the client and AP can initiate the authentication process equally and even simultaneously. Even if a password or key is compromised, WPA3 personal offers forward secrecy, which prevents attacker from being able to use a key to unencrypt data that has already been transmitted over the air.
Regarding 802.1x authentication, the WPA versions do not require any specific EAP method.Instead, the Wi-Fi Alliance certifies interoperability with well known EAP methods like EAP-TLS, PEAP, EAP-TTLS, and EAP-SIM. Enterprise authentication is more complex to deploy than personal mode because authentication servers must be
set up and configured as a critical enterprise resource.
The Personal mode of any WPA version is usually easy to deploy in a small environment or with clients that are embedded in certain devices because a simple text key string is all that is needed to authenticate the clients. Be aware that every device using the WLAN must be configured with an identical pre-shared key. If you ever need to update or change
the key, you must touch every device to do so. As well, the pre-shared key should remain a well kept secret; you should never divulge the pre-shared key to any unauthorized person.
You should always select the highest WPA version that the clients and wireless infrastructure in your environment will support.